-
 chevron_right
chevron_right
Hollywood, Netflix, and Apple Are Behind Latest Pirate ‘Brand’ Blockades in Belgium
news.movim.eu / TorrentFreak • 2 January 2026 • 3 minutes
 In Belgium, the Department for Combating Online Infringement is responsible for overseeing the local pirate site blocking efforts.
In Belgium, the Department for Combating Online Infringement is responsible for overseeing the local pirate site blocking efforts.
The department reviews injunctions from the Business Court in Brussels and translates these into concrete blockade implementation orders.
The first blockade of this kind was announced in April 2025 and predominantly targeted sports streaming websites. Notably, however, these blocking requirements were not limited to ISPs; they also compelled DNS resolvers to comply.
These DNS resolvers, including Google and Cloudflare, were not pleased, and Cisco’s OpenDNS even went as far as stopping its service in Belgium to avoid having to meddle with DNS. This backlash apparently struck a nerve, as OpenDNS has since resumed its activities in Belgium as the case is under appeal.
U.S. Movie Giants Behind New Blocking Push
Meanwhile, other rightsholders joined in, with various book publishers securing a blocking order against shadow libraries last August. In late November, this was followed by a new blocking order targeting various movie piracy sites , such as 1337x and Soap2day.
Interestingly, this order is rather limited in its scope. Instead of casting a wide net, it strictly targets Belgium’s five major Internet Service Providers: Proximus, Telenet, Orange Belgium, DIGI Communications Belgium, and Mobile Vikings.
While the targeted ISPs and the blocked sites were listed in the implementation order, the requesting rightsholders were not mentioned.
However, after the Belgian government responded to our transparency request just before Christmas, we can now reveal that familiar names are behind the latest site-blocking campaign.
The underlying order from the French-speaking Business Court in Brussels lists a coalition of major studios: Disney, Netflix, Sony, Paramount, Universal, and Warner Bros. These companies, all members of the Motion Picture Association (MPA), are joined by another video entertainment giant: Apple.

The MPA has been a driving force behind site-blocking efforts around the world, so it is no surprise to see this activity in Belgium too. However, that doesn’t make the order any less interesting.
Ten Pirate Brands
While we now have access to the underlying order, the formal list of URLs (Annex 1) will remain confidential. The same is true for Annex 2.b., the official list of the ten pirate names or brands.
“In addition to the list of ‘target sites’ provided in Annex 1 of their application, the applicants also submit an Annex 2.a., classified as confidential, in which the applicants explain the phenomenon of pirate brands, before providing, in Annex 2.b, a list of 10 names,” the translated order reads.

These brands are important because the court order mandates that any future sites using this name or branding are also eligible for a spot on the blocklist.
While this list remains confidential, Belgium’s piracy blocklist is transparently published online. This includes the recently blocked URLs, from which it is not difficult to compile the likely list of blocked pirate brands. These include 1337x , Fmovies , Soap2day , Sflix , FlixHQ , Papadustream , French-Strea m, Coflix and Wiflix .
American DNS Questions
The underlying court order further confirms that these heavyweight movie studios did not include any third-party DNS providers (like Google or Cloudflare) in their list of intermediaries. Whether this is motivated by the ongoing appeal in other Belgian blocking cases or a strategic shift remains unknown.
It appears that, for now, the movie companies currently prefer a more targeted approach, focusing exclusively on major Internet Service Providers.
Depending on the motivation, this choice can have implications beyond Belgium. In the United States, rightsholders, including these same movie studios, continue to push for site-blocking legislation , which they hope to see implemented this year. Thus far, we have seen proposed site-blocking bills with and without DNS resolvers, so it can go either way.
—
A copy of the order (RR/25/00092) from the French-speaking Business Court of Brussels is available with minor redactions of personal information here (pdf) .
From: TF , for the latest news on copyright battles, piracy and more.



 As the
As the
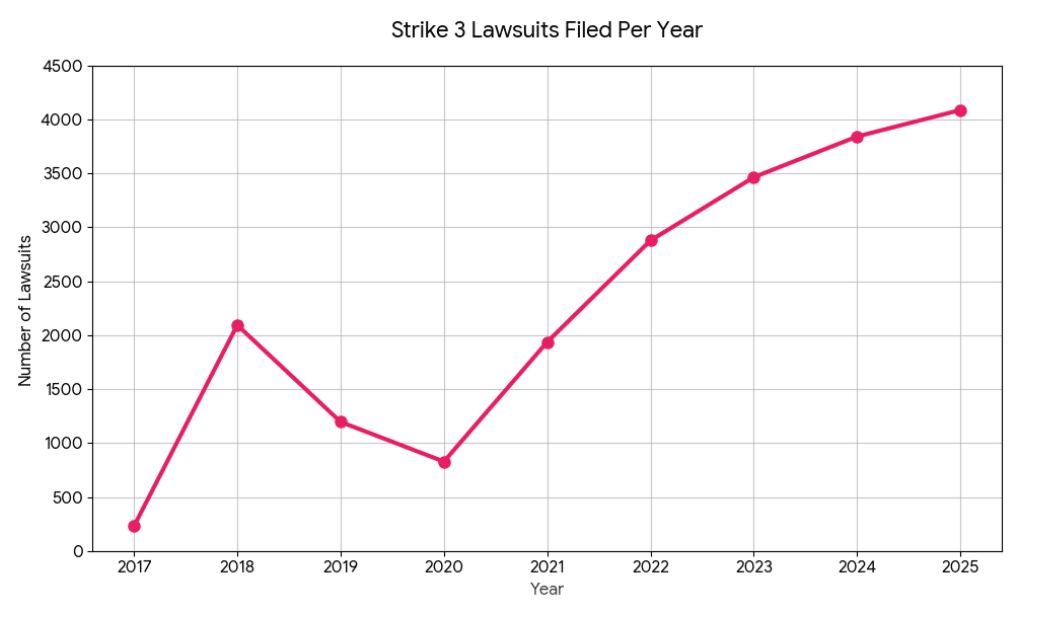
 For writers and readers, news often comes and goes, with major headlines swiftly fading into the background.
For writers and readers, news often comes and goes, with major headlines swiftly fading into the background.
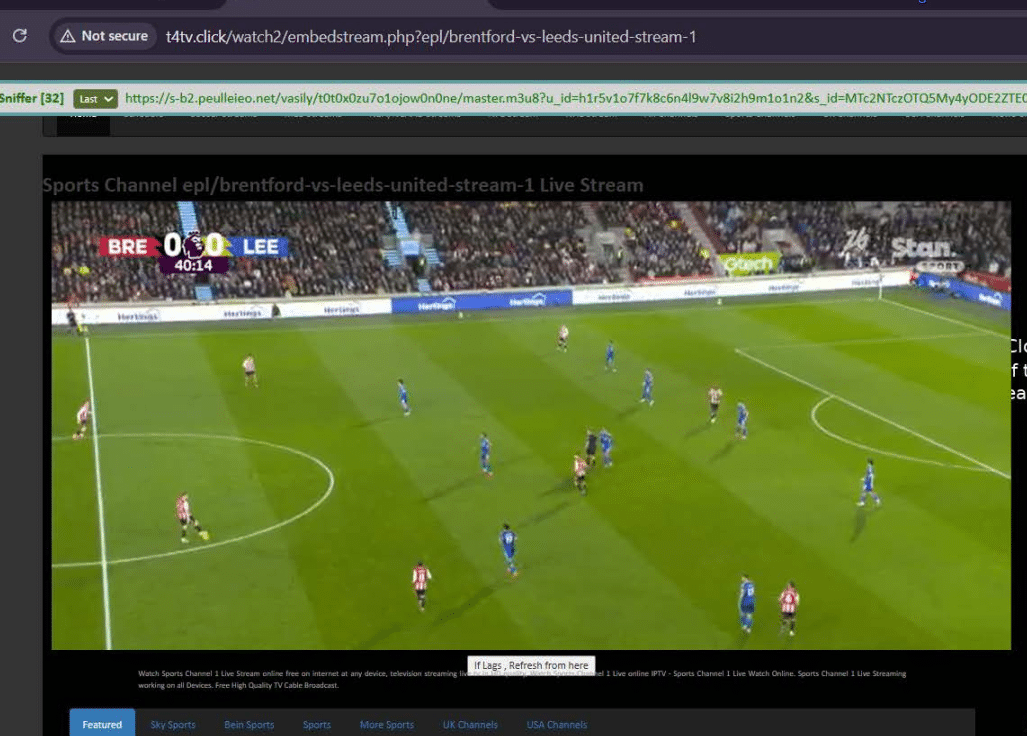
 As England’s top football competition, the
As England’s top football competition, the
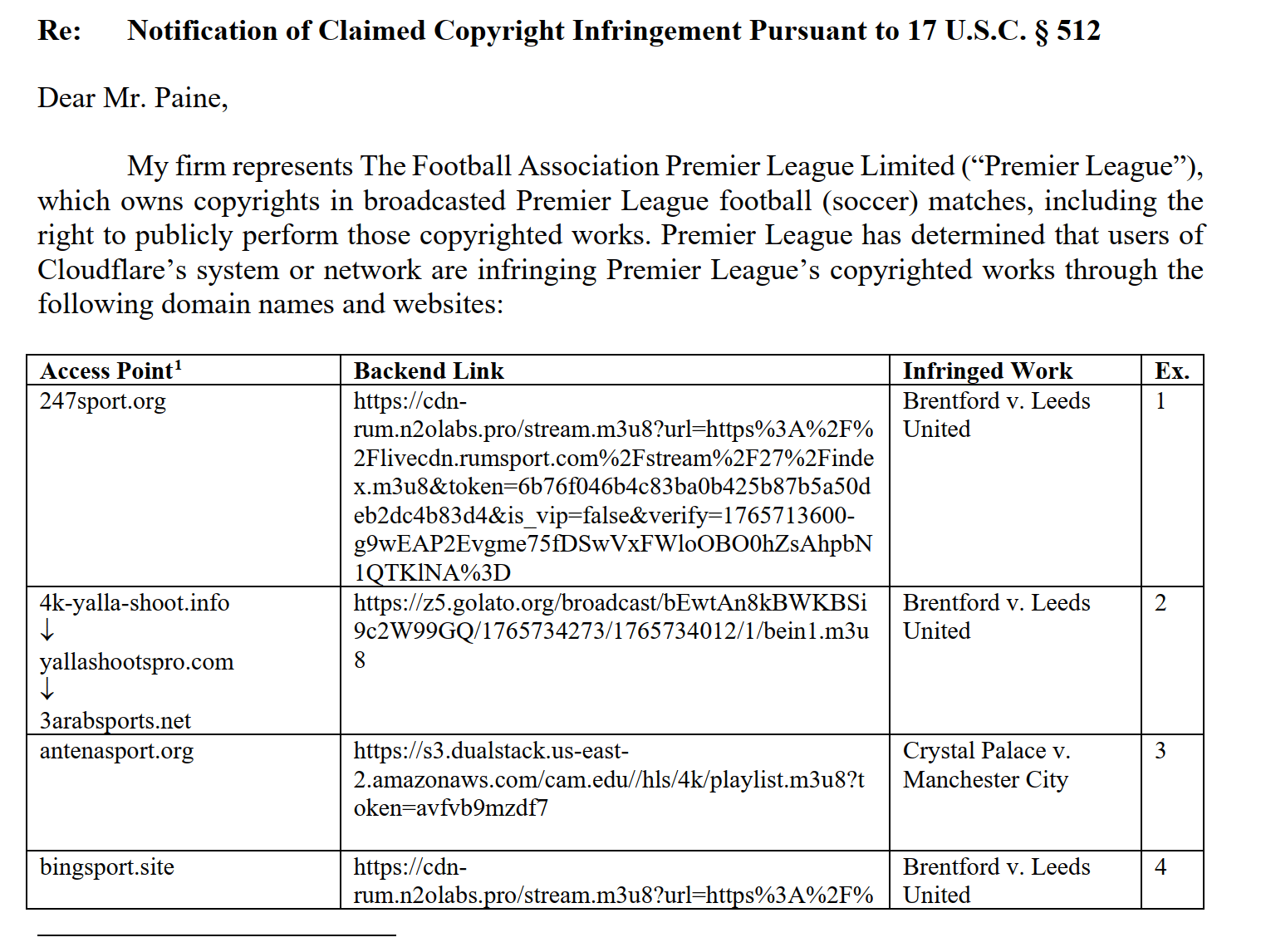

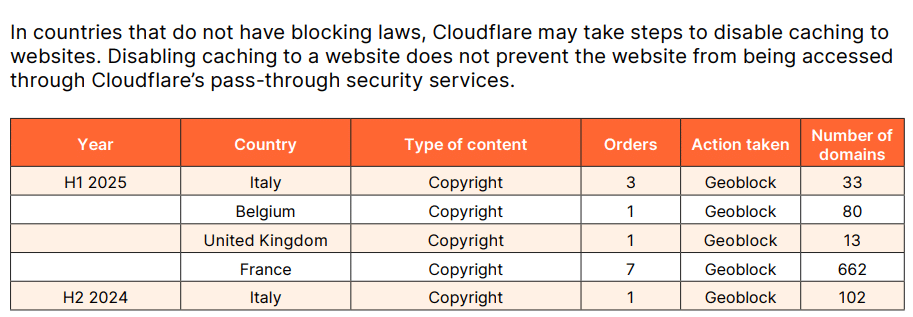
 As one of the leading Internet infrastructure companies,
As one of the leading Internet infrastructure companies,

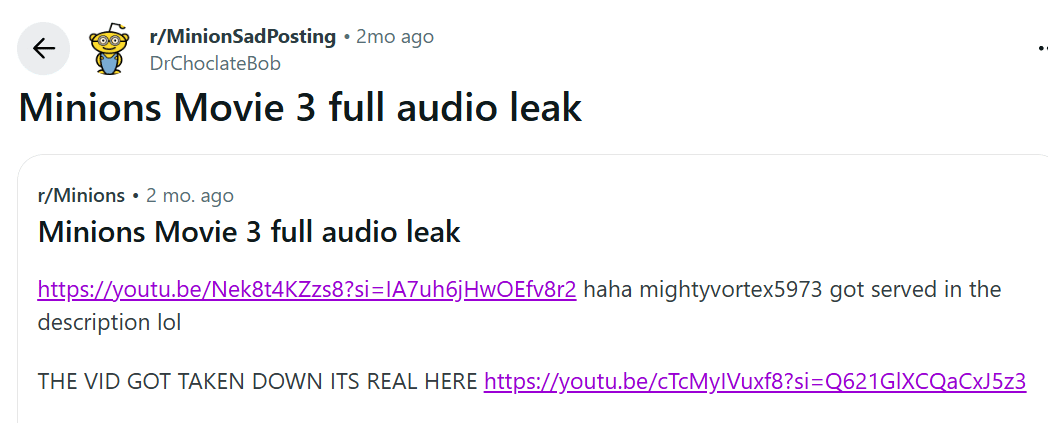
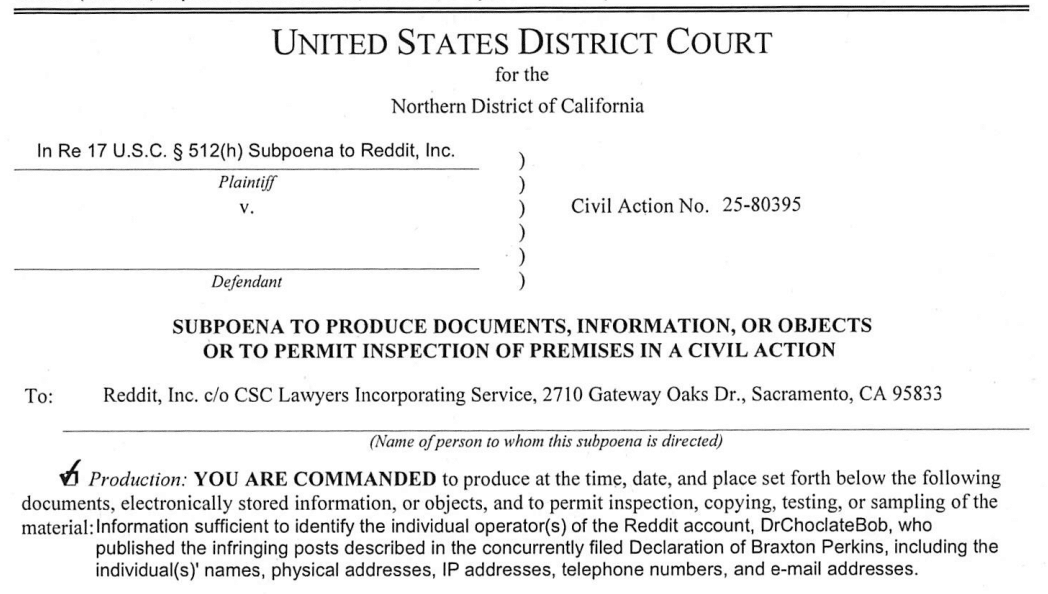
 In October, several Reddit posts appeared online that supposedly linked to a leaked copy of the Minions 3 audio.
In October, several Reddit posts appeared online that supposedly linked to a leaked copy of the Minions 3 audio.