-
chevron_right
The XMPP Standards Foundation: The XMPP Newsletter September 2022
news.movim.eu / PlanetJabber • 1 October, 2022 • 8 minutes
Welcome to the XMPP Newsletter, great to have you here again! This issue covers the month of September 2022.
Like this newsletter, many projects and their efforts in the XMPP community are a result of people’s voluntary work. If you are happy with the services and software you may be using, especially throughout the current situation, please consider saying thanks or help these projects! Interested in supporting the Newsletter team? Read more at the bottom.
Newsletter translations
This is a community effort, and we would like to thank translators for their contributions. Volunteers are welcome! Translations of the XMPP Newsletter will be released here (with some delay):
- English (original): xmpp.org
- French: jabberfr.org and linuxfr.org
- German: xmpp.org and anoxinon.de
- Italian: nicfab.it
- Spanish: xmpp.org
XSF Announcements
-
The XSF membership application period for the fourth quarter 2022 is currently open. If you are interested in becoming a XSF member then you can apply for membership . Please submit by November 27, 2022.
-
The XSF Board and Council application period for the next year is currently open. If you are interested in running for the XSF Board or XSF Council then you can apply here . Please submit by November 6, 2022. Remind that XMPP Council members must be elected members of the XSF; however, there is no such restriction for the Board of Directors.
-
Security advisory: libexpat before 2.4.9 is vulnerable to CVE-2022-40674 , make sure to update, if you depend on it.
Google Summer of Code 2022
The Google Summer of Code 2022 finished! The two new contributors Patiga and PawBud were working on open-source software projects in the XMPP environment. Read their all their blog posts, too. Thanks everyone for participation!
-
Patiga worked on more flexible file transfers in Dino . Mentors are fiaxh and Marvin W. .
-
PawBud worked towards adding support for A/V communication via Jingle in ConverseJS . Mentors are JC Brand and vanitasvitae .
XSF fiscal hosting projects
The XSF offers fiscal hosting for XMPP projects. Please apply via Open Collective . For more information, see the announcement blog post . Current projects:
Events
- XMPP Office Hours : available on our YouTube channel
- Berlin XMPP Meetup (remote) : monthly meeting of XMPP enthusiasts in Berlin, every 2nd Wednesday of the month
- Capitole du Libre : Members of the “JabberFR” and “Libre en Communs” associations will be present in Toulouse on the 19-20th of November
Articles
Congrats to the Monal developers for the new NLnet Funding that will cover privacy enhancements for the push servers, an explorative audio and video calls implementation, UI updates for MUC and Contact views, and SASL updates.
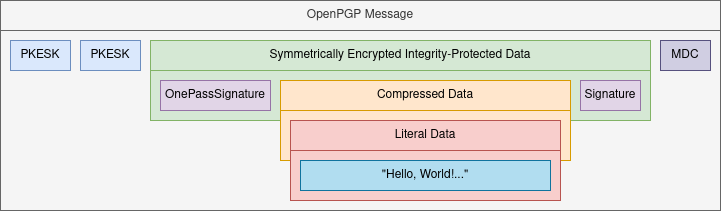
Paul Schaub wrote a blog post focused on the technical details of how to check the validity of nested packet sequences using pushdown automata. This technique will be used in a partial rework of PGPainless to validate OpenPGP messages. Earlier this month another post on “Creating a Web-of-Trust Implementation: Accessing Certificate Stores” has been published, too.
jmp.chat brought voicemail changes and opt-in Jabber ID discoverability to their service, along with an updated Android app and new custom F-Droid repos for both stable and pre-release versions. Furthermore, they wrote about “Privacy and Threat Modelling” in general.
Arnaud wrote about updates on the chatty server and HTTPAuthentificationOverXMPP .
Anoxinon.media published their blogpost XMPP - Teil 1 - Messaging mal anders [DE].
Software news
Clients and applications
Maintenance release of Beagle IM 5.3.1 that fixes sending OMEMO encrypted files and entering password-protected MUC. Besides, Tigase launched a new, simpler website tigase.org that makes it easier to access open-source projects created by Tigase.
Gajim 1.5.0 and 1.5.1 have been released . These releases come with a significant performance boost. Pinned chats can be ordered via drag and drop, message corrections have been improved, and many bugs have been fixed.
An OMEMO 2 implementation has just been merged to Libervia , coming with Stanza Content Encryption ( XEP-0420 ) support, thanks to the great work of Syndace, author or python-omemo (which has been updated in the process). One of the major benefits is that other Stanza elements can now be encrypted too, not only the body. OX ( XEP-0373 / XEP-0374 ) should follow soon, exciting times!
While Monal development is going forward, see the funding news above, and they deployed new Push servers as announced in the July 2022 XMPP Newsletter, users of old Monal versions would need to update, so if you or your contacts didn’t already the developers urge you to do it now .
Missed in the August 2022 XMPP Newsletter was a release of UWPX, the XMPP client for UWP (Windows 10) devices. While version v.0.43.0.0 has only a fixup it’s unfortunately also the Final Update as the developer is stepping away from the project. Maintainers to follow-up are welcome to reach out!
Kaidan, a user-friendly and modern chat app for every device, will receive a grant by NLnet for adding encrypted audio and video calls . Congratulations!
Servers
Jackal v0.62.0 is out bringing XEP-0313 Message Archive Management support and several enhancements.
Metronome IM 4.0 has been released . This version introduces Lua 5.3 support, a revamped shared API for group chats stanza archiving, MIX Core/PAM experimental support, Message Moderation support and support for containerization.
Profanity 0.13.0 has been released.
Libraries & Tools
python-nbxmpp 3.2.2 and 3.2.3 have been released , adding a stringprep implementation and improvements for detecting broken TCP connections.
The first beta of Slidge (XMPP bridges) is out!: Slidge, supporting Signal, Telegram, Discord, Steam, Mattermost, Facebook and Skype. Currently only direct messages are supported, but development is going further. Find the article in English and French .
Work on XMPP ⇔ ActivityPub gateway (supported by a NLnel funding) has been achieved. The gateway supports features such as following/followers, favourite/like (or “noticed” in XMPP terms , reactions (compatible with Pleroma ), mentions, sharing/reboost and lastly events (compatible with Mobilizon ). It has been tested with Mastodon , Pleroma and Mobilizon. It’s still considered alpha quality, a blog post should follow soon to explain in more details .
Ignite Realtime Community:
- REST API Openfire plugin 1.10.0 has been released
- New Openfire plugin: Push Server
Extensions and specifications
Developers and other standards experts from around the world collaborate on these extensions, developing new specifications for emerging practices, and refining existing ways of doing things. Proposed by anybody, the particularly successful ones end up as Final or Active - depending on their type - while others are carefully archived as Deferred. This life cycle is described in XEP-0001 , which contains the formal and canonical definitions for the types, states, and processes. Read more about the standards process . Communication around Standards and Extensions happens in the Standards Mailing List ( online archive ).
xmpp.org features a page about XMPP RFCs as well.
Proposed
The XEP development process starts by writing up an idea and submitting it to the XMPP Editor. Within two weeks, the Council decides whether to accept this proposal as an Experimental XEP.
-
Events
- This specification describes how to handle calendar events with XMPP
New
- No new XEP this month.
Deferred
If an experimental XEP is not updated for more than twelve months, it will be moved off Experimental to Deferred. If there is another update, it will put the XEP back onto Experimental.
- No XEPs deferred this month.
Updated
-
Version 0.4.0 of
XEP-0440
(SASL Channel-Binding Type Capability)
- Make sasl-channel-binding element a top level stream feature (dg)
Last Call
Last calls are issued once everyone seems satisfied with the current XEP status. After the Council decides whether the XEP seems ready, the XMPP Editor issues a Last Call for comments. The feedback gathered during the Last Call can help improve the XEP before returning it to the Council for advancement to Stable.
- No Last Call this month.
Stable
- No XEP moved to stable this month.
Deprecated
- No XEP deprecated this month.
Call for Experience
A Call For Experience - like a Last Call, is an explicit call for comments, but in this case it’s mostly directed at people who’ve implemented, and ideally deployed, the specification. The Council then votes to move it to Final.
- No Call for Experience this month.
Spread the news!
Please share the news on other networks:
Subscribe to the monthly XMPP newsletter
SubscribeAlso check out our RSS Feed !
Looking for job offers or want to hire a professional consultant for your XMPP project? Visit our XMPP job board .
Help us to build the newsletter
This XMPP Newsletter is produced collaboratively by the XMPP community. Therefore, we would like to thank Adrien Bourmault (neox), alkino, anubis, Benoît Sibaud, emus, goffi, Jeybe, Licaon_Kter, martin, MattJ, MSavoritias (fae,ve), nicfab, Ppjet6, vanitasvitae, wurstsalat, Zash for their support and help in creation, review, translation and deployment. Many thanks to all contributors and their continuous support!
Each month’s newsletter issue is drafted in this simple pad . At the end of each month, the pad’s content is merged into the XSF Github repository . We are always happy to welcome contributors. Do not hesitate to join the discussion in our Comm-Team group chat (MUC) and thereby help us sustain this as a community effort. You have a project and want to spread the news? Please consider sharing your news or events here, and promote it to a large audience.
Tasks we do on a regular basis:
- gathering news in the XMPP universe
- short summaries of news and events
- summary of the monthly communication on extensions (XEPs)
- review of the newsletter draft
- preparation of media images
- translations
License
This newsletter is published under CC BY-SA license .

